In general SSH protocol can be used for two purposes, file transfers and terminal access. SSH File Transfers. File transfers are primary focus of WinSCP. WinSCP supports SFTP (SSH File Transfer Protocol) for secure file transfers. In addition to that it also supports legacy SCP (Secure Copy Protocol). (02) Add Target Hosts#1 (03) Add Check Plugins#1 (04) Set Metric Collection Check (05) Visualize with Grafana (06) Add Check Plugins#2 (07) Add Check Plugins (08) Add Check Plugins (09) Add Check Plugins; Nagios (01) Install Nagios (02) Notification Setting (03) Set Thresholds (04) Add Monitoring Target Item (05) Add Monitoring Target Host#1.
From charlesreid1
- 1SSH Service Info
- 1.1Metasploit SSH Exploits
- 2Brute Force ssh_login
- 3Private Key ssh_login_pubkey
- 3.1Obtaining Private Key
First, a reminder of the information nmap returned about the SSH service after a port scan:
This server isn't using the 1.0 protocol, which is hopelessly broken and easy to defeat. This means getting past SSH will be (at least) mildly challenging.
Metasploit SSH Exploits
Two SSH attacks using metasploit:
- ssh_login
- ssh_login_pubkey
Metasploit ssh_login
The first attack is ssh_login, which allows you to use metasploit to brute-force guess SSH login credentials.
- Module name is
auxiliary/scanner/ssh/ssh_login
Link: https://www.offensive-security.com/metasploit-unleashed/scanner-ssh-auxiliary-modules/
Metasploit ssh_login_pubkey
The second attack requires a private key. If you do gain access to the private SSH keys on a victim machine, you can attempt to authenticate with a large number of hosts and services using that private key.
- Module name is
auxiliary/scanner/ssh/ssh_login_pubkey
Link: https://www.offensive-security.com/metasploit-unleashed/scanner-ssh-auxiliary-modules/
We already covered how to brute force the login with Hydra, Metasploitable/SSH/Brute Force
Did you know you can also brute force an SSH login with Metasploitable? Use the auxiliary/scanner/ssh/ssh_login module.
Setting Up the Attack
We will use the module auxiliary/scanner/ssh/ssh_login:
Set this to run on the Metasploitable virtual box target:
Running the Attack
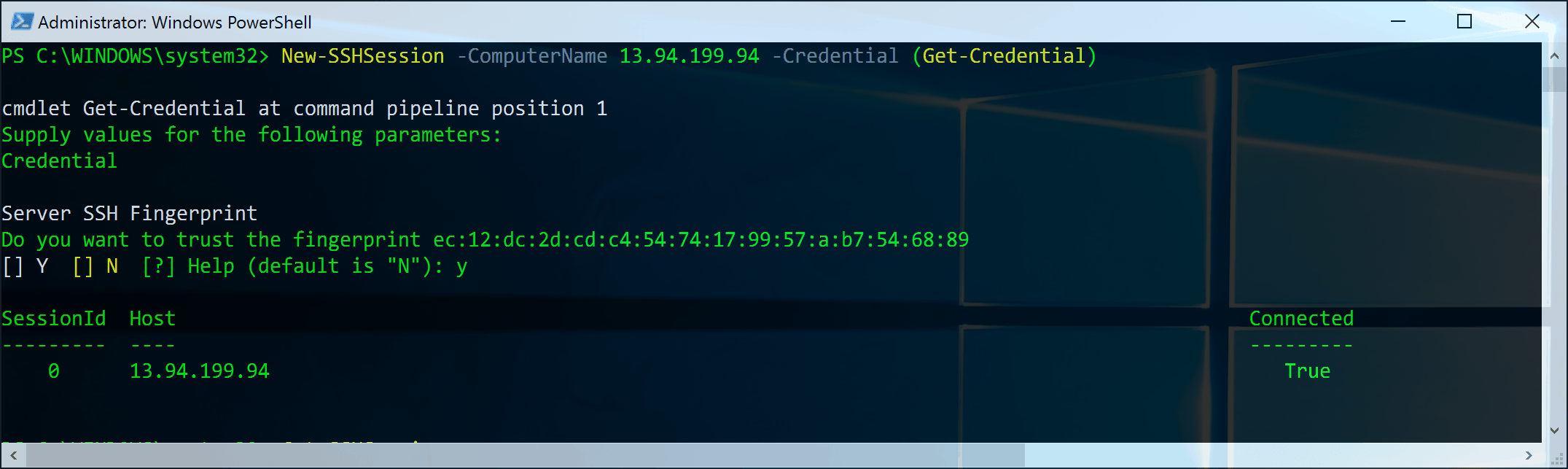
Now run the attack:
Houston, We Have A Shell
At this point, we can create a session with the machine that we compromised. Logged in as user msfadmin:
If you manage to get your hands on the victim's private key, the auxiliary/scanner/ssh/ssh_login_pubkey module is for you!
This module uses the private key to do two things:
Ssh Copy 17 03 13
- Get access to the victim machine
- Get access to any machines that trust the victim's private key (must be listed in the SSH files of the victim machine)
Obtaining Private Key
To carry out this attack, you will need to have access to the file system, and/or be able to mount the remote file system (which, on Metasploitable, happens to be possible!): see Metasploitable/NFS
Once you've got access to the file system, you'll grab a copy of the remote machine's private keys, and use them together with Metasploit to obtain access to the machine.
(Note that you could also plant your keys on the target, by adding your public SSH keys onto the target machine's list of trusted machines, but this technique would restrict you to a particular machine, wile the Metasploit method is portable and less intrusive.)
To snatch the target's private key:
Now you have a copy of the msfadmin account's private SSH key.
Metasploit We'll use Metasploit to turn this into access to the remote machine.
This key is also useful for impersonating the target when connecting to OTHER remote machines.
Planting Private Keys
An alternative method to gain access, although it is not useful for gaining access to any machines other than the victim machine, is to GENERATE a public/private SSH key pair from the attacker machine, and copy the PRIVATE key over to the remote machine. (Using the public key and the above-mentioned technique would be easier, but it's worth mentioning at least.)
To plant your private keys on the remote machine, you'll need write access to the target user's home directory. You'll generate a public SSH key from the attacker machine, the machine you want to have access WITH, and add it to the other machine's ~/.ssh/authorized_keys.
Now run the attack:
Houston, We Have A Shell
At this point, we can create a session with the machine that we compromised. Logged in as user msfadmin:
If you manage to get your hands on the victim's private key, the auxiliary/scanner/ssh/ssh_login_pubkey module is for you!
This module uses the private key to do two things:
Ssh Copy 17 03 13
- Get access to the victim machine
- Get access to any machines that trust the victim's private key (must be listed in the SSH files of the victim machine)
Obtaining Private Key
To carry out this attack, you will need to have access to the file system, and/or be able to mount the remote file system (which, on Metasploitable, happens to be possible!): see Metasploitable/NFS
Once you've got access to the file system, you'll grab a copy of the remote machine's private keys, and use them together with Metasploit to obtain access to the machine.
(Note that you could also plant your keys on the target, by adding your public SSH keys onto the target machine's list of trusted machines, but this technique would restrict you to a particular machine, wile the Metasploit method is portable and less intrusive.)
To snatch the target's private key:
Now you have a copy of the msfadmin account's private SSH key.
Metasploit We'll use Metasploit to turn this into access to the remote machine.
This key is also useful for impersonating the target when connecting to OTHER remote machines.
Planting Private Keys
An alternative method to gain access, although it is not useful for gaining access to any machines other than the victim machine, is to GENERATE a public/private SSH key pair from the attacker machine, and copy the PRIVATE key over to the remote machine. (Using the public key and the above-mentioned technique would be easier, but it's worth mentioning at least.)
To plant your private keys on the remote machine, you'll need write access to the target user's home directory. You'll generate a public SSH key from the attacker machine, the machine you want to have access WITH, and add it to the other machine's ~/.ssh/authorized_keys.
This presumes the .ssh directory exists. If it doesn't exist, you can make it, and tamper with the filesystem.
Setting Up the Attack
Here's info on the auxiliary/scanner/ssh/ssh_login_pubkey module in Metasploit, which will carry out the attack:
Set some options, such as the private key file, the username to log in with, and the remote host:
Running the Attack
Execute the attack, to use the remote machine's private key to gain access to the remote machine:
Success - we've got a session. Master of typing – tutor 1 2 3rd edition.
Getting a Shell
Now we can use the sessions command to utilize the information we just found and set up an interactive session.
We could create more mischief, by copying everyone else's private SSH keys and SSH connection histories, potentially giving us passwordless access to additional machines.
We could also get busy with post-exploit activities.
See https://www.offensive-security.com/metasploit-unleashed/scanner-ssh-auxiliary-modules/
Table of Contents
- about ssh
- secure shell
- /etc/ssh/
- ssh protocol versions
- public and private keys
- rsa and dsa algorithms
- log on to a remote server
- executing a command in remote
- scp
- setting up passwordless ssh
- ssh-keygen
- ~/.ssh
- id_rsa and id_rsa.pub
- copy the public key to the other computer
- authorized_keys
- passwordless ssh
- X forwarding via ssh
- troubleshooting ssh
- sshd
- sshd keys
- ssh-agent
- practice: ssh
- solution: ssh
The secure shell or ssh is a collection of tools using a secure protocol for communications with remote Linux computers.
This chapter gives an overview of the most common commands related to the use of the sshd server and the ssh client.
Avoid using telnet, rlogin and rsh to remotely connect to your servers. These older protocols do not encrypt the login session, which means your user id and password can be sniffed by tools like wireshark or tcpdump. To securely connect to your servers, use ssh.
The ssh protocol is secure in two ways. Firstly the connection is encrypted and secondly the connection is authenticated both ways.
An ssh connection always starts with a cryptographic handshake, followed by encryption of the transport layer using a symmetric cypher. In other words, the tunnel is encrypted before you start typing anything.
Ssh Copy 17 03 18
Then authentication takes place (using user id/password or public/private keys) and communication can begin over the encrypted connection.
The ssh protocol will remember the servers it connected to (and warn you in case something suspicious happened).
The openssh package is maintained by the OpenBSD people and is distributed with a lot of operating systems (it may even be the most popular package in the world).
Configuration of ssh client and server is done in the /etc/ssh directory. In the next sections we will discuss most of the files found in /etc/ssh/.
The ssh protocol has two versions (1 and 2). Avoid using version 1 anywhere, since it contains some known vulnerabilities. You can control the protocol version via /etc/ssh/ssh_config for the client side and /etc/ssh/sshd_config for the openssh-server daemon.
The ssh protocol uses the well known system of public and private keys. The below explanation is succinct, more information can be found on wikipedia.
Imagine Alice and Bob, two people that like to communicate with each other. Using public and private keys they can communicate with encryption and with authentication.
Ssh Copy 17 03 17
When Alice wants to send an encrypted message to Bob, she uses the public key of Bob. Bob shares his public key with Alice, but keeps his private key private! Since Bob is the only one to have Bob's private key, Alice is sure that Bob is the only one that can read the encrypted message.
When Bob wants to verify that the message came from Alice, Bob uses the public key of Alice to verify that Alice signed the message with her private key. Since Alice is the only one to have Alice's private key, Bob is sure the message came from Alice.
This chapter does not explain the technical implementation of cryptographic algorithms, it only explains how to use the ssh tools with rsa and dsa. More information about these algorithms can be found here:
The following screenshot shows how to use ssh to log on to a remote computer running Linux. The local user is named paul and he is logging on as user admin42 on the remote system.
As you can see, the user paul is presented with an rsa authentication fingerprint from the remote system. The user can accepts this bu typing yes. We will see later that an entry will be added to the ~/.ssh/known_hosts file.
The user can get log out of the remote server by typing exit or by using Ctrl-d.
This screenshot shows how to execute the pwd command on the remote server. There is no need to exit the server manually.
The scp command works just like cp, but allows the source and destination of the copy to be behind ssh. Here is an example where we copy the /etc/hosts file from the remote server to the home directory of user paul.
Here is an example of the reverse, copying a local file to a remote server.
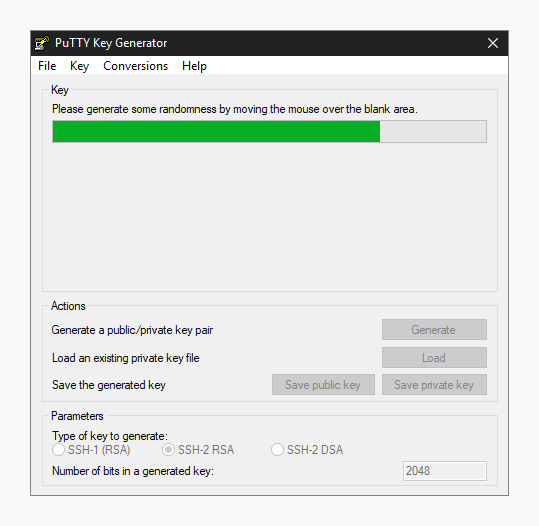
Cisdem video player 4 2 0 download free. To set up passwordless ssh authentication through public/private keys, use ssh-keygen to generate a key pair without a passphrase, and then copy your public key to the destination server. Let's do this step by step.
In the example that follows, we will set up ssh without password between Alice and Bob. Alice has an account on a Red Hat Enterprise Linux server, Bob is using Ubuntu on his laptop. Bob wants to give Alice access using ssh and the public and private key system. This means that even if Bob changes his password on his laptop, Alice will still have access.
Ssh Copy 17 03 15
The example below shows how Alice uses ssh-keygen to generate a key pair. Alice does not enter a passphrase.
You can use ssh-keygen -t dsa in the same way.
While ssh-keygen generates a public and a private key, it will also create a hidden .ssh directory with proper permissions. If you create the .ssh directory manually, then you need to chmod 700 it! Otherwise ssh will refuse to use the keys (world readable private keys are not secure!).
As you can see, the .ssh directory is secure in Alice's home directory.
Bob is using Ubuntu at home. He decides to manually create the .ssh directory, so he needs to manually secure it.
The ssh-keygen command generate two keys in .ssh. The public key is named ~/.ssh/id_rsa.pub. The private key is named ~/.ssh/id_rsa.
The files will be named id_dsa and id_dsa.pub when using dsa instead of rsa.
To copy the public key from Alice's server tot Bob's laptop, Alice decides to use scp.
Be careful when copying a second key! Do not overwrite the first key, instead append the key to the same ~/.ssh/authorized_keys file!
Alice could also have used ssh-copy-id like in this example.
In your ~/.ssh directory, you can create a file called authorized_keys. This file can contain one or more public keys from people you trust. Those trusted people can use their private keys to prove their identity and gain access to your account via ssh (without password). The example shows Bob's authorized_keys file containing the public key of Alice.
Alice can now use ssh to connect passwordless to Bob's laptop. In combination with ssh's capability to execute commands on the remote host, this can be useful in pipes across different machines.
Another popular feature of ssh is called X11 forwarding and is implemented with ssh -X.
Below an example of X forwarding: user paul logs in as user greet on her computer to start the graphical application mozilla-thunderbird. Although the application will run on the remote computer from greet, it will be displayed on the screen attached locally to paul's computer.
Use ssh -v to get debug information about the ssh connection attempt.
The ssh server is called sshd and is provided by the openssh-server package.
The public keys used by the sshd server are located in /etc/ssh and are world readable. The private keys are only readable by root.
When generating keys with ssh-keygen, you have the option to enter a passphrase to protect access to the keys. To avoid having to type this passphrase every time, you can add the key to ssh-agent using ssh-add.
Most Linux distributions will start the ssh-agent automatically when you log on.
This clipped screenshot shows how to use ssh-add to list the keys that are currently added to the ssh-agent
0. Make sure that you have access to two Linux computers, or work together with a partner for this exercise. For this practice, we will name one of the machines the server.
1. Install sshd on the server
2. Verify in the ssh configuration files that only protocol version 2 is allowed.
3. Use ssh to log on to the server, show your current directory and then exit the server.
4. Use scp to copy a file from your computer to the server.
5. Use scp to copy a file from the server to your computer.
6. (optional, only works when you have a graphical install of Linux) Install the xeyes package on the server and use ssh to run xeyes on the server, but display it on your client.
7. (optional, same as previous) Create a bookmark in firefox, then quit firefox on client and server. Use ssh -X to run firefox on your display, but on your neighbour's computer. Do you see your neighbour's bookmark ?
8. Use ssh-keygen to create a key pair without passphrase. Setup passwordless ssh between you and your neighbour. (or between your client and your server)
9.Verify that the permissions on the server key files are correct; world readable for the public keys and only root access for the private keys.
10. Verify that the ssh-agent is running.
11. (optional) Protect your keypair with a passphrase, then add this key to the ssh-agent and test your passwordless ssh to the server.
0. Make sure that you have access to two Linux computers, or work together with a partner for this exercise. For this practice, we will name one of the machines the server.
1. Install sshd on the server
2. Verify in the ssh configuration files that only protocol version 2 is allowed.
3. Use ssh to log on to the server, show your current directory and then exit the server.
4. Use scp to copy a file from your computer to the server.
5. Use scp to copy a file from the server to your computer.
6. (optional, only works when you have a graphical install of Linux) Install the xeyes package on the server and use ssh to run xeyes on the server, but display it on your client.
7. (optional, same as previous) Create a bookmark in firefox, then quit firefox on client and server. Use ssh -X to run firefox on your display, but on your neighbour's computer. Do you see your neighbour's bookmark ?
8. Use ssh-keygen to create a key pair without passphrase. Setup passwordless ssh between you and your neighbour. (or between your client and your server)
9. Verify that the permissions on the server key files are correct; world readable for the public keys and only root access for the private keys.
10. Verify that the ssh-agent is running.
11. (optional) Protect your keypair with a passphrase, then add this key to the ssh-agent and test your passwordless ssh to the server.
